WordPress Maintenance, WordPress Support
WordPress 5.7.2 Security and Maintenance Release
- By WP Agents
27 Jan

“In May 2021, WordPress has updated its version by a security release known as WordPress 5.7.2 security and maintenance release.”
“In Dec 2021, WordPress platform has again released some new security updates known as WordPress 5.8.2 security and maintenance releases.”
Now the question is why the WordPress platform frequently releases security updates, and what are those?
On 13 May 2021, WordPress has released a security patch. It was for a Critical Object Injection vulnerability usually found in PHPMailer. Those vulnerabilities are known as CVE-2020-36326 and CVE-2018-19296.
PHPMailer & Security Patches in WordPress 5.7.2 Updates
Let me say what is PHPMailer first. It is the component, which WordPress uses to send an email by default. Functionally, it is an email library with the required components and security to send safe emails through PHP code from the webserver.
Technically, PHPMailer is safe because it doesn’t create any SQL at all and also doesn’t have anything to do with JavaScript. However, vulnerabilities are possible either with a header or mail attachment. Due to these concerns, a security patch was released to disable follow-up of the email path and impacts of attachments.
Origin of Vulnerabilities in Earlier Versions of WordPress 5.7.2
Previous versions of PHPMailer were allowing Phar Decentralization through addAttachment with a UNC pathname. Now, the issue has been mitigated by considering that path names are unreadable by PHPMailer. As a side effect, it has eliminated the code that blocked the exploitation of addAttachment.
We are aware of Object Injection attacks and the risks it poses. Object Injection vulnerability demands a “POP Chain” to do additional damages. However, the presence of POP Chain alone is not sufficient to exploit vulnerabilities, but PHPMailer allows injection of a PHP object.
Cure of Vulnerabilities through WordPress 5.7.2 Updates
With these security patches, this kind of direct access becomes a nightmare for hackers and security attackers. Now, all accesses happen through functionality exposed in the core and different plugins.
In the case of contact form plugins, which allow file attachments cannot be directly controlled by users to exploit the attachment path. If attackers want to exploit vulnerabilities, they need to apply the vulnerable magic method besides the presence of a plugin vulnerability.
Therefore, it is best to install the latest security updates and save your WordPress site from PHPMailer related security threats. If you are not familiar with such installation or facing some issues while updating your customized WordPress website, WP-Agents is a leading WordPress support and WordPress maintenance service provider at the global level.
About WordPress 5.8.2 Updates
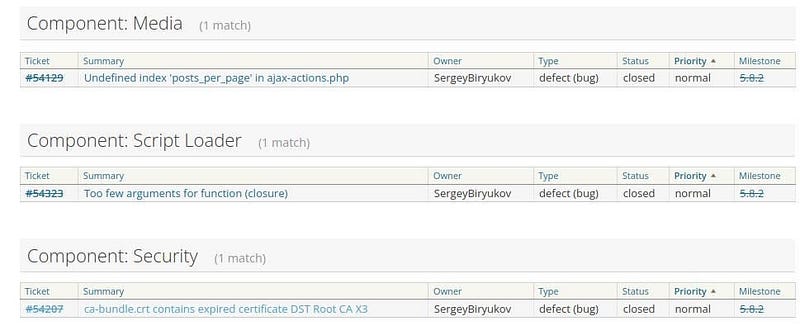
In the latest release of WordPress 5.8.2 updates, developers have fixed two bugs: media, script loader. Moreover, they have fixed one security issue known as “Expired certificate DST Root CA X3.”
The security issue was related to the SSL certificate. When a certificate expires and a new one is likely issued (Encrypt ACME client), an intermediate self-signed certificate (ISRG Root X1) has been displayed. Unfortunately, most operating systems contained this expire soon certificate and displayed as a security error.
Now, the issue has been fixed with the new security release WordPress 5.8.2 security and maintenance.
At WP-Agents
We at WP-Agents, keep our loyal patrons informed with the latest security updates and also help them incorporate those security updates by providing WordPress support and WordPress maintenance services with suitable plans.
In the case of extreme customization of themes and WordPress core, our help becomes mandatory to incorporate such security issues. We take care of the entire customized website using our exceptional skills in WordPress updates and customization.